Fake It ‘til We Make It: The Art of Windows User Space Emulation
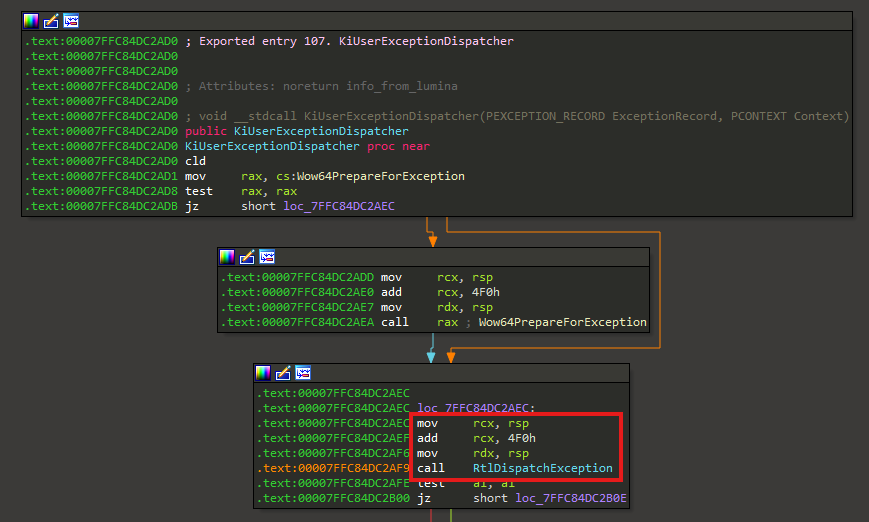
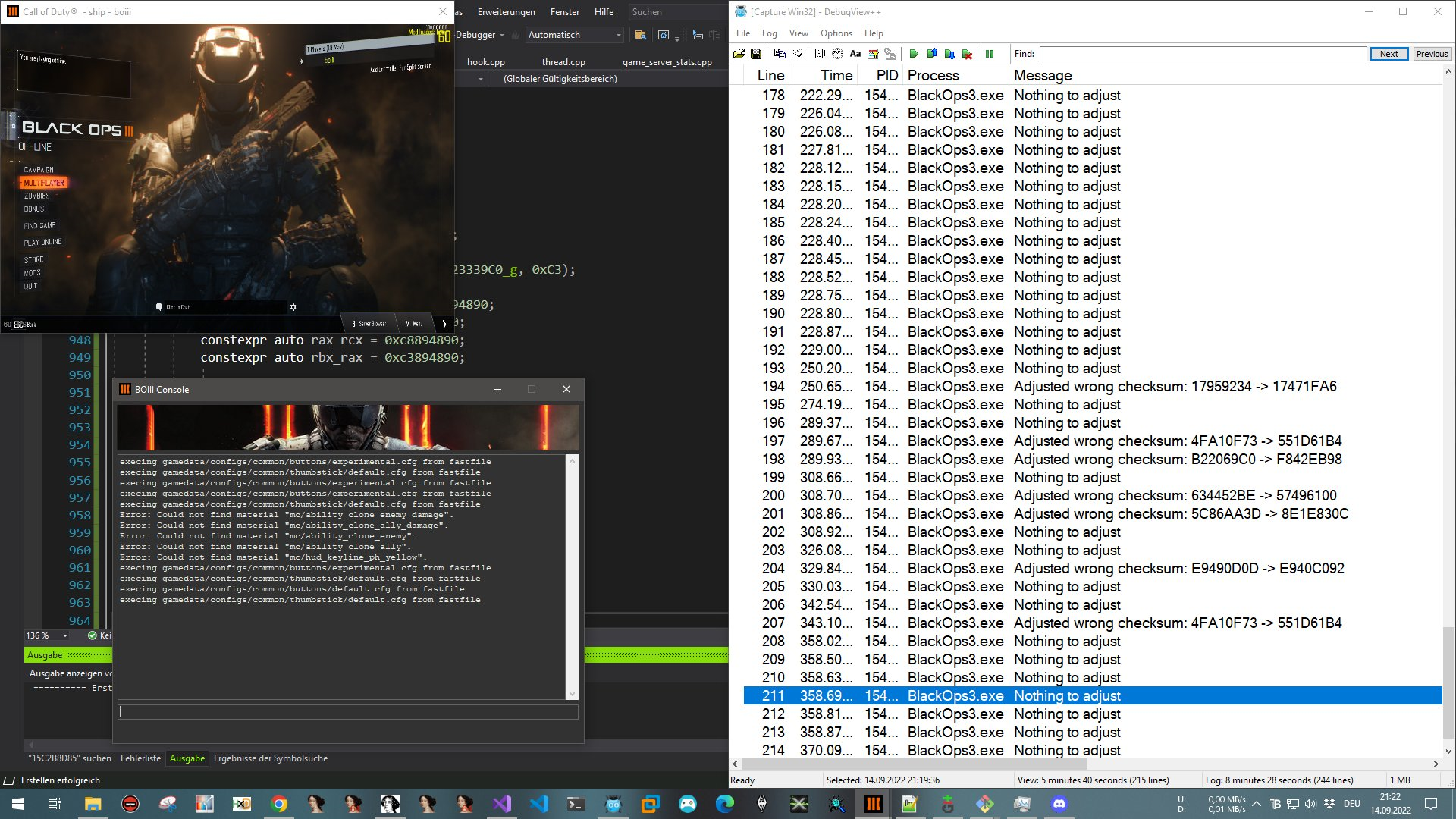
Talk at Navaja Negra 2024 Modern software systems are becoming increasingly complex, making thorough analysis a daunting task. Add advanced DRM and obfuscation technologies into the mix, and the challenge grows exponentially. In this presentation, we’ll explore the development of a Windows user-space emulation framework designed to tackle these complexities head-on. We’ll discuss how emulation can be a powerful tool for analyzing and overcoming the obstacles posed by intricate software and robust DRM protections. You’ll gain insights into the technical aspects of building an emulation layer and learn how this approach benefits both security researchers and DRM analysts. If you’ve ever wondered how to “fake it” in a world full of complex protections, this talk will show you how emulation can be your secret weapon. ...