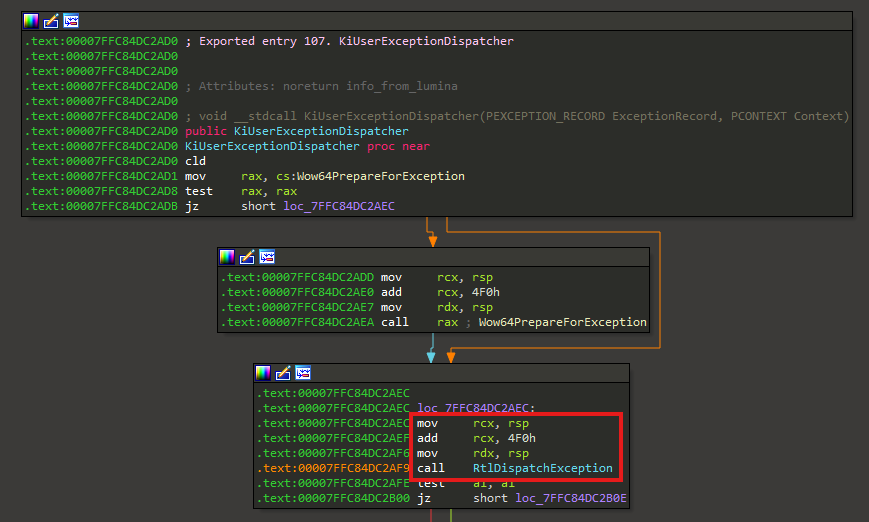
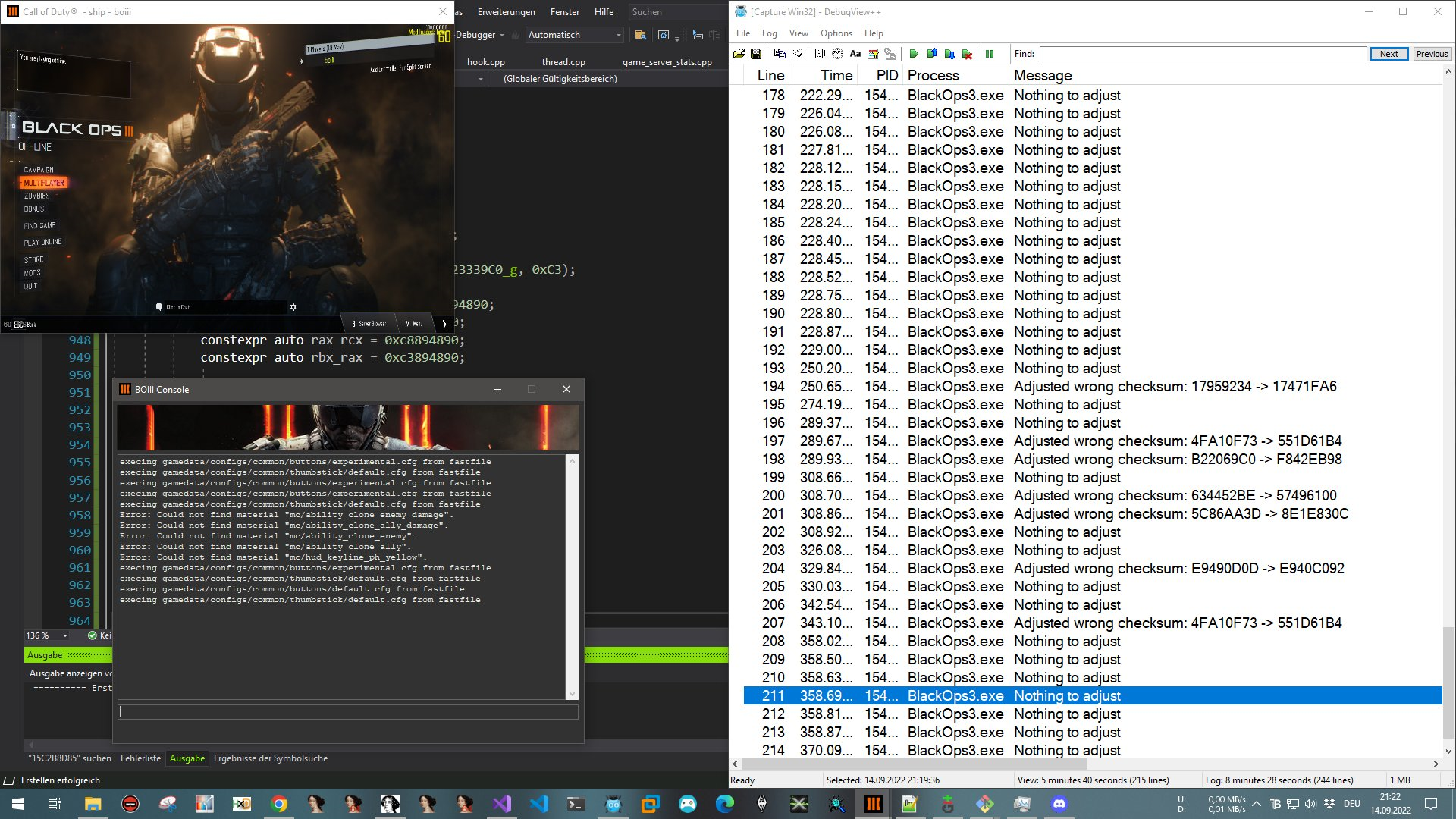
Reverse Engineering Denuvo in Hogwarts Legacy
Talk at Navaja Negra 2025 This technical presentation explores the inner workings of Denuvo Anti-Tamper, one of the gaming industry’s most widely deployed DRM solutions. Through detailed reverse engineering analysis, we’ll examine Denuvo’s protection mechanisms, obfuscation techniques, and architectural design choices. The talk covers the methodology used to analyze the system, key findings about how it integrates with game executables, and insights into modern anti-tamper technology. Attendees will gain a deeper understanding of contemporary DRM implementations and the technical challenges involved in software protection systems. ...